Having closed brick-and-mortar operations on March 16, 2020 for safety reasons, the nearly overnight shift to a purely e-commerce revenue model brought uncertainty. However, a rapid uptick in online sales provided a sense of relief, albeit short-lived.
Our client became concerned when a closer look at the online transactions revealed an unusually large volume of electronic gift card purchases made using their private label credit card. Dan Ryan, payment card industry (PCI) forensic investigator (PFI) and Kroll’s leading expert in payment card fraud said, “you should see some increase in transactions because of the move to e-commerce but instead some days had a 10-, 20- or 30-fold increase in purchases of electronic gift cards.”
Converting Electronic Gift Cards to Cash
Retailer private label credit cards function like a typical credit card but are custom branded with the retailer’s logo and are only valid for retailer-specific purchases, including the retailer’s electronic gift cards. These electronic gift cards are most often purchased in pre-defined dollar amounts (e.g., $50, $100 and $200) whereby the transaction value is stored on the electronic gift card. Electronic gift card numbers are then emailed to the recipient who normally uses them to purchase goods at the retailer.
Without proper controls in place, this process is susceptible to both private label credit card fraud and gift card fraud. Malicious actors are known to sell stolen private label credit card and retailer electronic gift card numbers on the dark web at a discounted rate. Dark web buyers use them to fraudulently purchase retailer goods, which may be kept or resold for cash.
Due to the alarming increase in purchases of electronic gift cards using their private label credit card, the retailer called us in to conduct a credit card fraud investigation and better understand what was happening. We initially focused on determining how cybercriminals may have gained access to the private label cards used to make these purchases. Although the initial suspicions revolved around the customer’s private label card data being compromised, our investigation couldn’t pinpoint how or where a compromise may have happened.
Exploring the Private Label Cards Authorization Process
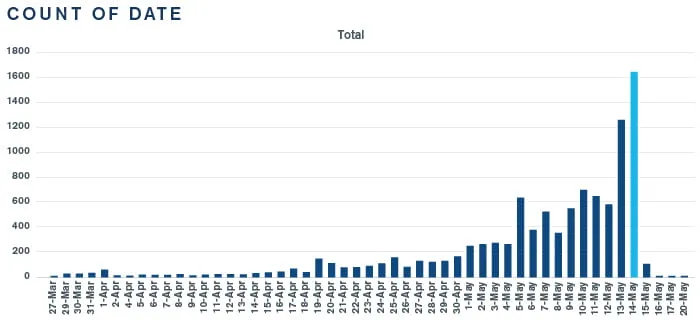
Ryan continued, as shown in the graphic “over the course of the post-COVID-19 jump in electronic gift card purchases, about $1.5 million of those were purchased.” After a closer analysis we discovered hundreds of transactions that were all being sent only to a handful of email addresses, which was very suspicious.
We focused on determining if there was a compromised data set that was full of private label account information to include primary account number (PAN), expiry and card verification value (CVV). The Kroll team questioned whether the cards had been compromised somewhere else in an “attempt to understand where in the heck threat actors got the cards to even conduct these transactions,” said Ryan.

In walking through the authorization process with the issuer of the private label cards to the retailer, we discovered that there really wasn't a compromised data set in this case at all.
Our investigation revealed the merchant’s private card issuer only used the PAN when authorizing transactions; neither the electronic gift card’s expiry nor CVV were checked. This meant that if a cybercriminal only had the 16-digit string that constitutes the PAN they could use that information for purchases.
"the merchant’s private card issuer only used the PAN when authorizing transactions; neither the gift card’s expiry nor CVV were checked.."
“With a bin (bank identification number) range, which is public knowledge, [a cybercriminal] can just use an account number generator to generate card numbers,” cautioned Ryan. This process will produce a series of random card numbers, some that are valid, which in this case is exactly what had taken place. What started out feeling like a data breach turned into a poorly configured process for transaction authorizations that allowed threat actors to convert these randomly generated electronic gift card numbers into cash.
Technical and Contractual Remediation
Although this case demonstrates the value of engaging a PFI such as Ryan when things go wrong, engaging a PFI before an incident occurs is encouraged to help reduce risk. Kroll PFIs can help clients minimize the chances of private label credit card and electronic gift card fraud by proactively working to:
- Conduct PCI DSS assessments;
- Identify possible PCI DSS violations;
- Discover card transaction processing vulnerabilities and weaknesses; and
- Recommend technical, administrative and physical controls to reduce risk.
As far as the card brands and the merchant processor are concerned, the buck stops with the merchant. It does not matter who the merchant retains for the private label. Although the merchant would then have a right to seek recompense from the private label issuer, who wants a right of indemnity, Kroll would prefer clients not have the liability in the first place.
A careful review of agreements with credit card issuers, merchant processors and other involved in processing payment card data is one of the first steps a merchant should take to protect themselves from card transaction fraud. We recommend merchants have a very thorough understanding of their merchant processor contracts, and of course, ensure basic security controls are in place for transaction authorizations such as verifying the PAN, expiry and CVV for all transactions. Clients should also consider enlisting the help of a law firm that understands PCI requirements to ensure proper controls are defined and enforced in contracts.
This case study was extracted from the webinar COVID-19 and the Surge in Retail Threats, which also includes an overview of the PCI environment along with two additional case studies.
