With COVID-19 recognized as a pandemic, healthcare providers find themselves in uncharted territories trying to build out emergency response and contingency plans to address a potential influx of sick patients with the capacity to overload and break the healthcare industry.
As healthcare providers deal with the invisible threat of the virus, cybercriminals are already exploiting their vulnerabilities in an attempt to profit from this pandemic: on March 13, a cyberattack took down the network of a Czech Republic Hospital serving as a coronavirus testing facility and on March 16, a US Health Agency fielding coronavirus response suffered an unspecified cyberattack.
According to Kroll intake reports for 2019, healthcare was the most frequently targeted industry. Healthcare as a sector encompasses a variety of specialties from large hospital systems to health administration companies and medical laboratories. Kroll intakes for 2019 indicated that large hospital systems were the most frequently targeted by threat actors.
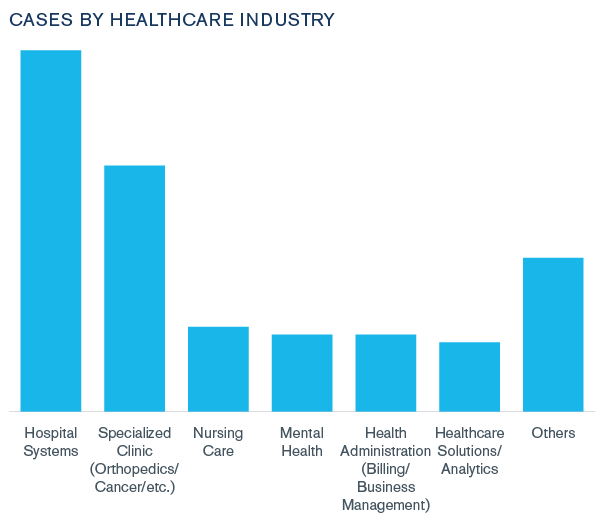
Figure 1: 2019 Targeted Healthcare Industry Disciplines
Email compromise and ransomware were the most observed threat incident types against the healthcare sector.
Hospital Systems and the Ransomware Threat
With ransomware activity on the rise, such distributors may see the coronavirus pandemic as an easy route to gouging hospital systems or clinics of a significant ransom demand to avoid outages of critical services.
In one Kroll case, a Managed Service Provider (MSP) spread Sodinokibi ransomware to its clients, including one who ran a surgical clinic. Due to this encryption, the surgeon was locked out of critical procedural and patient information related to diagnostics and ambulatory care.
“Threat actors prey on targets who are likely to pay their ransom demands. In this climate, hospitals must ensure continuity of services to treat impacted patients. Hit by such a critical attack that disrupts access to patient medical records, they may seriously consider paying an exorbitant ransom,” notes Keith Wojcieszek, managing director in Kroll’s Cyber Risk practice.
Additionally, in this new climate of ransomware exfiltration, Kroll has observed cases where threat actors who encrypt specialty clinics go after the individual patients threatening to publicly expose their private medical record data including photographs or history of drug use. “One can imagine a future state scenario where threat actors may try to further extort healthcare entities by claiming to expose an individual patient’s COVID-19 diagnosis,” continues Wojcieszek.
Mitigating Ransomware
As detailed in issue 2 of the Monitor, Kroll’s threat intelligence newsletter, experts Devon Ackerman and Pierson Clair recommend focusing on:
- Offline, encrypted backups frequently tested and monitored
- Routine assessments, including vulnerability and penetration testing
- Endpoint monitoring, detection and response
- Prevent public access to the Service Message Block (SMB/port 445) and the Remote Desktop Protocol (RDP/port 3389)
- File integrity monitoring configured for trusted locations
Email Compromise and Coronavirus Information
Email compromise was the most observed threat incident type against the healthcare sector in 2019. An email compromise typically starts with a believable phishing email that appears to be from a trusted source but can actually inject malware if users click on the embedded files or links.
At a time when news about the coronavirus pandemic is changing on an hourly basis, it is likely that employees at healthcare institutions will be anticipating frequent alerts about coronavirus status from their own organization as well as external news providers and third-party vendors.
Multiple coronavirus-themed phishing campaigns have been observed in recent months, prompting the Cybersecurity and Infrastructure Security Agency (CISA) to issue a warning on March 6 for users to “exercise caution” in handling any email with a COVID-19 related subject line.
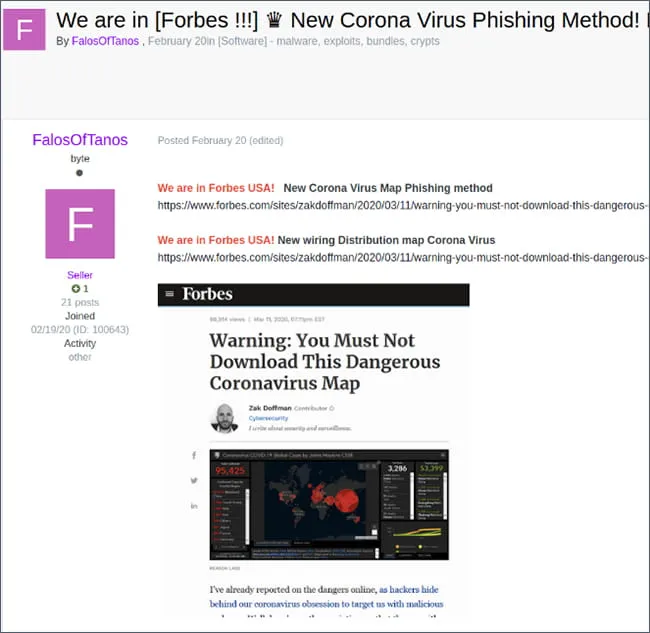
Figure 2 : Threat Actors Brag about Corona Phish
One of the most widely reported coronavirus phishing lures involves a dynamic map published by John Hopkins University meant to show the spread of the disease. Threat actors created a phishing lure emulating the map that is actually malicious. As open source reports about this campaign arose, threat actors selling it for $300 on cybercriminal forum, Exploit, updated their sales thread to brag about the fact that they had been featured in Forbes magazine.
Addressing Email Compromise Attacks
The social engineering deployed in modern email attacks forces organizations to look beyond technology to mitigate potental threats. On the technical side, Kroll experts recommend:
- Implement multi-factor authentication for email and sensitive applications, especially if they hold any patient health information
- Harden email system configuration, especially for cloud services like Office 365 and Google Suite
- Efforts to build a strong security culture, aware of common email threats, also require:
- Frequent phishing training, including guidance on spoofed domains
- Social media awareness education
Unprecedented Crisis, Expected Threats
As the coronavirus crisis pressures healthcare workers to build new procedures to deal with a global pandemic, security professionals should monitor developments relating to crisis response and cyber threats in anticipation of ransomware, social engineering and other attacks. If our experts can help you assess and manage the risks to your business, contact us as soon as possible. Additional guidance is available in our Coronavirus Resource Center.


