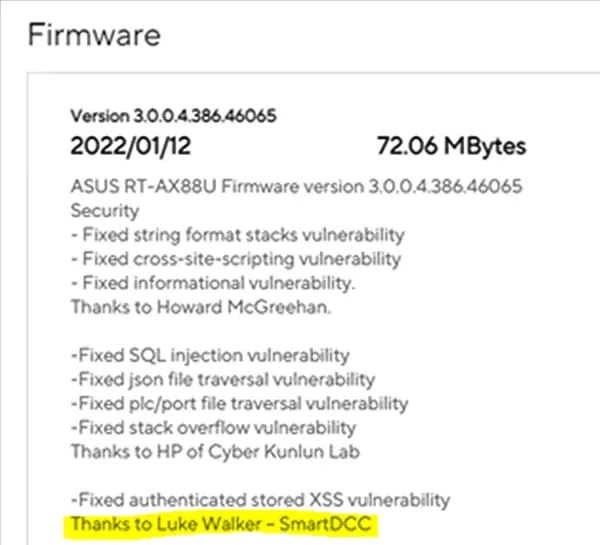
While studying for my master's degree in cyber security, I co-authored a paper regarding the rollout of IoT devices and the security considerations that businesses need to address to ensure these devices are secure. The paper underscored how a large majority of IoT devices used vulnerable components and did not follow basic secure programming principles.
As I was setting up my own new internal network in September 2021, I stumbled upon various logging functionalities within the custom deployment of DD-WRT that raised questions in my mind. DD-WRT, or in this case ASUSWRT, is a custom-developed Linux-based operating system for consumer router/modem products. Developed internally by ASUSTek, ASUSWRT builds on the standard DD-WRT distribution with a custom web interface and additional features, such as ASUSTek AiMesh networking products. The web front-end is programmed in ASP, which acts as a user interface for controlling various settings within the NVRAM of the device.
I had previously looked at router firmware but never found any vulnerabilities as such. Intrigued by the potential security-related issues that could occur if my router was hijacked, I set one of my Wi-Fi radios to a basic XSS payload to see if it had been sanitized...
|
“><script>alert(1)</script> |
Nope, no popup...
I moved on, considering that there would be no way an XSS would be present within a software package that is so widely deployed across the world, until...
A few days later, my ISP was playing up, so I logged in to the router and navigated to the log section of the platform to see if there were any issues on my side with the router. I quickly clicked through the menus provided, one being “Wireless logs.” I suddenly had a JavaScript popup in my browser window: My original XSS had fired under the log page.
Win!
Why Does This Matter?
ASUS routers have a functionality named Remote Management that allows for users to connect back to their home routers over HTTP, over port 8443. This also allows users to attach devices, such as USB pen drives, to their router to effectively turn it into a router/network attached storage combo unit.
An attacker with pre-existing access to a router could use this vulnerability to maintain persistence to the router, even after a password reset/IP address change. An attacker could additionally leverage this exploit to change any setting on the router, including Wi-Fi passwords and DNS servers, and enabling telnet/SSH. Ultimately, this exploit allows for complete takeover of a compromised router when chained with basic Unix knowledge.
It would be trivial to create a Shodan search query to pull in all ASUS router products accessible from the internet (Figure 1) (Table 1). Although the user must set their own password from the default one provided by the manufacturer to first access the web admin interface, cybercriminals know all too well that users commonly reuse passwords.
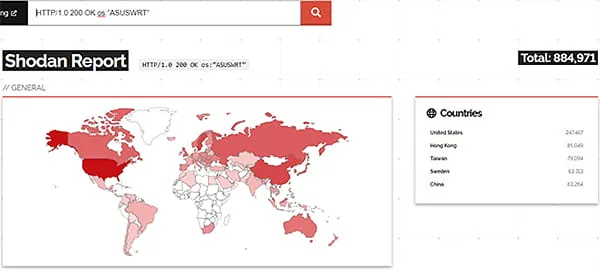
Figure 1 – Exposed ASUS Routers Globally