Many organizations focus on addressing the risks within their internal attack surface while overlooking the potential threats created by their external digital footprint on the surface, deep and dark web. This article outlines how companies can significantly mitigate this risk by combining digital risk protection with their detection and response approach.
An effective detection and response capability is essential for monitoring key assets and ensuring that they are comprehensively defended. Traditional detection and response strategies focus on detecting threats as early as possible during an attack, with the aim of containing and eradicating them before they can cause damage. Despite continuous investment in their internal defenses, businesses continue to fall victim to persistent cyberattacks. This is because they overlook their external defenses in addressing the risks associated with all levels of the internet.
Organizations have a greater chance of reducing the likelihood and impact of an attack if they can extend their detection efforts into their external digital footprint across the surface, deep and dark web. Companies intending to use or currently using managed threat detection and response (MDR) services can benefit by combining them with digital risk protection. By adding external sources into their threat detection and response strategy, they can extend visibility into the earliest stages of an attack, reconnaissance and resource development tactics as well as the post-compromise stages of an attack (such as extortion or the sale of IP, as shown in Figure 1).
Figure 1: Digital risk protection provides additional coverage of adversary tactics before and after a compromise.
What is Digital Risk Protection?
Digital risk protection is a branch of threat intelligence that provides pre- and post-compromise visibility by continuously monitoring the surface, deep and dark web for potential signs of targeted attacks or existing data leakage on parts of the web that are hidden from search engines, unindexed or obfuscated in closed communities.
Pre-compromise, being armed with this type of intelligence can help security teams enhance their defenses on the basis of greater clarity on exactly who is planning to attack the organization and how they plan to do it.
Post-compromise, this insight can provide security teams with early signs of a breach and enable them to take necessary action to limit its potential impact.
Digital Risk Protection also helps to protect brand reputation by scanning the surface web for brand misuse, impersonation and domain spoofing that could lead to threats against employees, customers and suppliers.
Why the Deep and Dark Web Should be Part of Your Threat Detection Strategy
With the deep and dark web making up approximately 96% of the internet that is unindexed, obscured or intentionally difficult to find, it’s no surprise that cybercriminals are constantly taking advantage of it to plan their attacks or sell stolen information onto persistent threat actors for further compromise. Dark web monitoring can play an important role in addressing the risk this creates for organizations.
What is Dark Web Monitoring?
Dark web monitoring provides a proactive, intelligence-driven approach for gauging exposure and defending against threats both before and after compromise. It works in three ways:
-
Pre-empting Targeted Attacks
A cyberattack doesn’t start on the network; it is planned in dark web forums and hacking sites, where threat actors conduct reconnaissance, sell company data to other threat actor groups and prepare resources to target their intended victim out of reach of cybersecurity teams and law enforcement.
Dark web intelligence provides security teams with the adversarial knowledge required to pre-empt and prevent attacks, reducing the reputational and financial impact of cybercrime on their business. -
Identifying a Past or Ongoing Breach
Discovering stolen customer lists or data, employee login credentials and email domains and IP addresses on the dark web can help your organization identify an ongoing data breach or a data breach that has occurred in the past. By identifying attacks (such as account takeovers or data leakage) at an earlier stage, businesses can mitigate the damage to their financial status and reputation. -
Mitigating Inherited Vulnerabilities or Exposures from Mergers/Acquisitions
As part of due diligence on a company that is a target for acquisition or merger, understanding the extent to which their sensitive data has been exposed can be critical information. The inadvertent exposure of that sensitive information can have a significant negative impact on the party or parties involved. This could include reputational damage, a decrease in the value of assets and even becoming the target for further cyberattacks.
Gaining this information after the merger or acquisition has been completed can also help to ensure that vulnerabilities or exposures are not inherited and that defenses are updated if an exposure or data leakage has occurred.
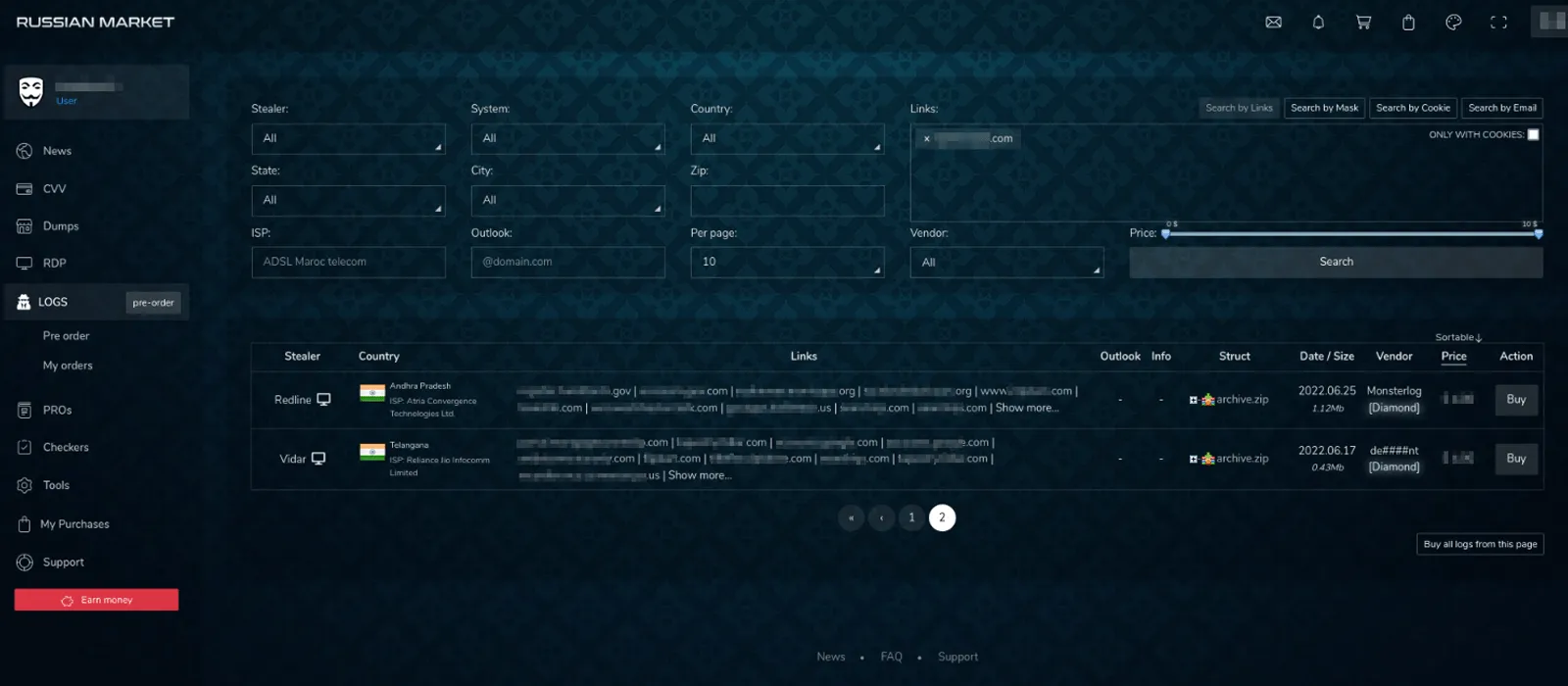
Figure 2: Russian Market is a marketplace where actors can buy listings which contain saved data from browser extensions (e.g. usernames, passwords, cookies). Once the actor buys the listing, they can then try to access those domains/resources using the saved information
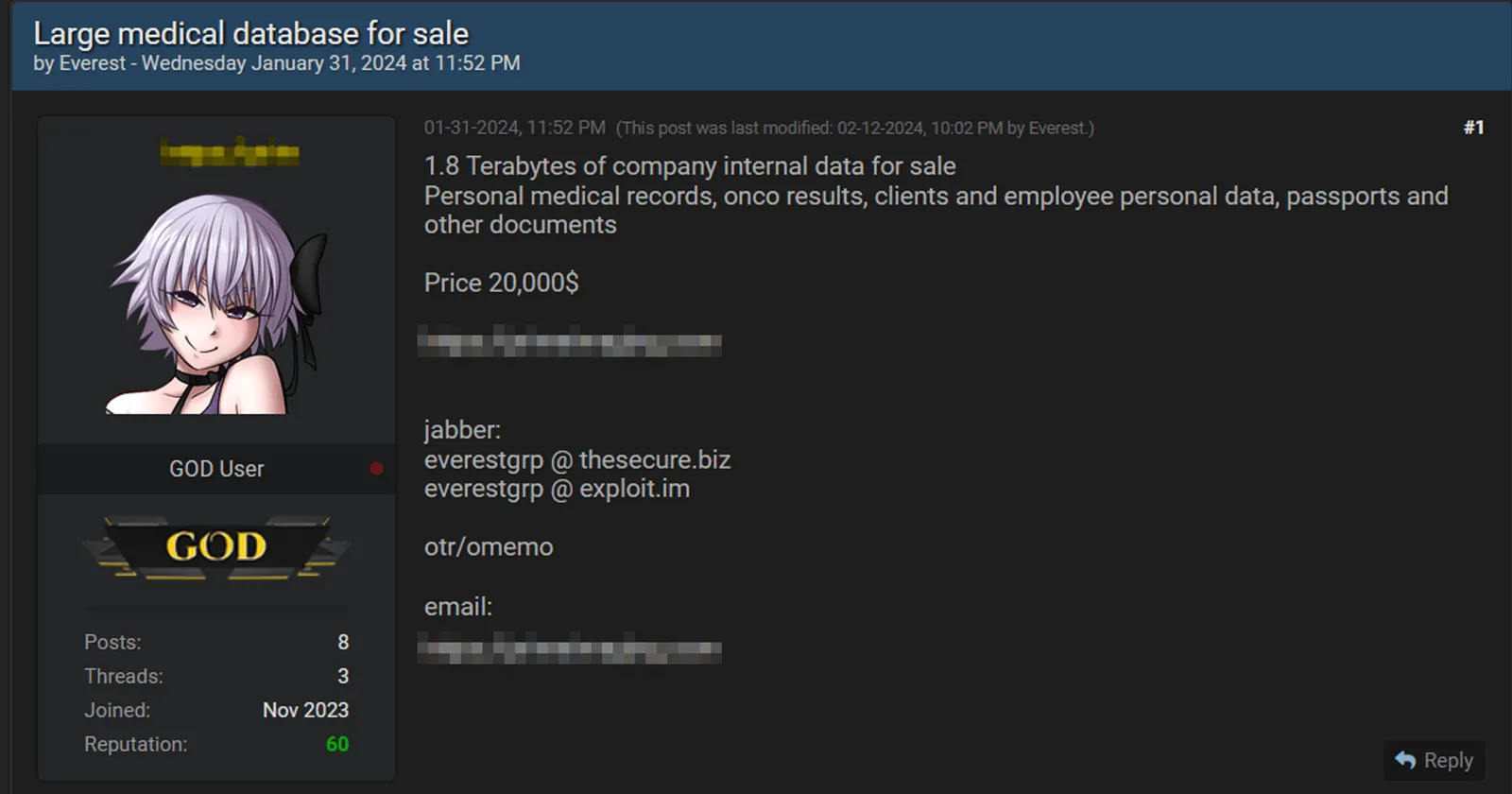
Figure 3: Medical database stolen from a health care provider being sold by a threat actor to the underground community
Why Use Surface Web Monitoring for Brand Protection?
Alongside the serious risks presented by the deep and dark web, organizations should also carefully monitor for those associated with the surface web. Integrating surface web within your threat detection and response strategy is especially valuable for organizations’ that rely heavily on brand reputation. This includes medium to large enterprises where company brand is a significant risk, such as retail and e-commerce companies, banking and finance institutions and industries holding highly sensitive data for multiple stakeholders (e.g., private equity, law firms, insurance and health care).
Attackers may target these types of businesses to create fake websites in their name or impersonate their domains to launch phishing attacks on their customers. Brand/domain monitoring can help organizations mitigate these risks by keeping track of the open web for domain impersonations, threats to company executives, spoofed websites and social media profiles.
However, as important as it is, monitoring is only one side of effective brand and domain defense. It should be followed with swift response using threat takedowns. This is where evidence is gathered and submitted as part of a formal request to the source platform owner, such as the internet service provider or platform owner for them to remove harmful content from the internet. As a time-consuming and specialized process, this should be managed by takedown experts with proven expertise in how to format and submit valid takedown requests to law enforcement, domain registrars and hosting sites.




