PYSA is the most recent ransomware variant known distributed by the Mespinoza Ransomware as a Service (RaaS) gang, which has been infecting victims since 2019. Kroll has consistently observed PYSA in our incident response engagements since 2020 and has noted an increase in frequency of this variant since the second quarter of 2021. Our analysis shows PYSA is opportunistic and not restricted to one sector or geographical area. PYSA primarily leverages exposed Remote Desktop Protocol (RDP) to gain a foothold into a network. Once inside a network, PYSA deploys several tools, including custom-built scripts written in GO language to maintain persistence. During their time in a network, the group focuses on exfiltration of data followed by encryption. Victims are then extorted for decryption services and to ensure that confidential information is not leaked.
Initial Access
Similarities across PYSA investigations such as tactics, infrastructure and the steady development of capabilities, suggests that the group is operated manually by a single group of actors. Initial access is usually gained through internet exposed RDP by using active, valid accounts. These accounts are accessed by brute force or previously exposed credentials from other breaches.
Once they have accessed a network, PYSA threat actors use discovery tactics to identify admins and other systems on the network. Tools such as AdvancedIPScanner and AdvancedPortScanner are commonly used during this process. PYSA will dump Local Security Authority Subsystem Service (LSASS) in order to gain enhanced privileges or further access to other privileged accounts before using Mimikatz to extract account information and passwords. Precursor PowerShell scripts are often run to disable anti-virus and other security mechanisms, the deletion of volume shadow copies, disable services and to identify documents of interest prior to encryption.
In our observation, loiter time for PYSA is longer than the average ransomware event, likely due to the manual nature of the attack. Earlier activity relied on maintaining access to valid accounts, however the group has recently been observed using a Golang tool known as Chisel to maintain command and control. The tool operates a tunnel over HTTP secured by Secure Shell (SSH)to pass through firewalls, allowing “hands-on” access to the target environment.
The main goal of a PYSA attack is extortion for data encryption and data leakage. They typically offer to decrypt and not leak stolen information if the victims pays the requested ransom. Once a network is encrypted, PYSA drops a ransom note (Readme.Read) and locks files with the extension .<domain> or .pysa. The ransomware binary writes the note to the registry key below, which displays the ransom note on logon.
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\legalnoticetext
PYSA Exfiltration Tactics, Techniques and Procedures
To locate documents for exfiltration, PYSA uses automated scanning of systems with PowerShell by using a script that searches 123 keywords. Files can contain personal identifiable information (PII), tax and financial information, login credentials, legal documents, incriminating evidence and other sensitive information. Exfiltration has been achieved through the mounting of file shares on adversary infrastructure and the use of tools such as WinSCP.
PSYA will post these files on their actor-controlled site, the home page of which advertises the slogan “Protect Your System Amigo.” (Figure 1) PYSA typically adds new victims 1-2 times per month with each “update” possibly including 5 to 20+ victims. Recently, the threat actors have implemented CAPTCHAs to the shaming site in order to view published exfiltrated data.
We have observed that the time lag between encryption and data publication is longer for PYSA than other ransomware variants. In some instances, Kroll has identified victims posted to the actor-controlled site upwards of three months past the date of encryption.

Figure 1 - PYSA Actor-Controlled Site Home Page (SOURCE: Kroll)
Victim Trends
Although the most common sector targeted is education, PYSA targeting includes a wide spectrum of sectors such as medical, manufacturing, construction, local government, transport and retail. This is not an all-inclusive list.
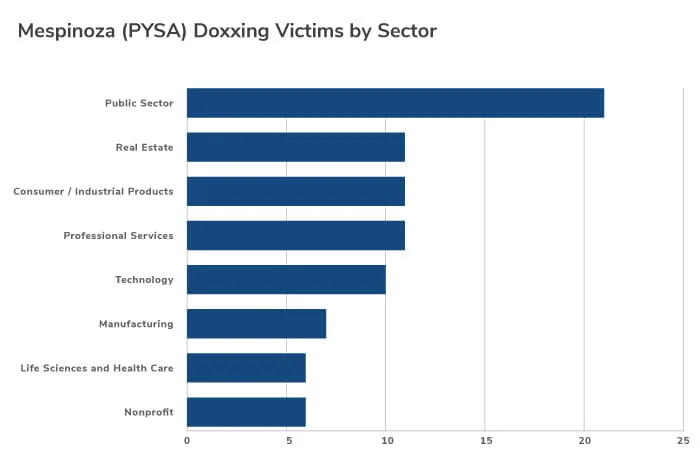
Figure 2 - PYSA Victims by Sector (Data Source: Intel471)
55% of victims are located within the United States. However, companies in other countries such as the United Kingdom, Brazil, Italy, Canada, and France have all faced numerous attacks.
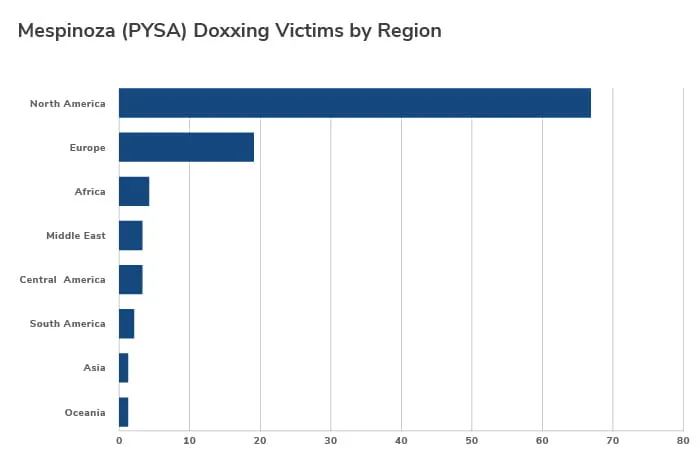
Figure 3 - PYSA Victims by Region (Data Source: Intel471)
Example Engagement
In a recent Kroll engagement, a multinational company in the food and beverage industry was targeted by PYSA and had their data exfiltrated and a ransom demanded. The initial access point for the threat actors was the organizations’ exposed RDP. One month after the initial access, ransomware was executed. Data exfiltration was conducted via a Server Message Block (SMB) protocol-based share to an internally hosted web server, where the adversary left the remote share over-exposed. This allowed the exfiltrated files to be viewed on PYSA’s server for a short while.
Experts Corner
Paul Wells and James Thoburn in our practice provide recommendations to keep your network secure and prevent PYSA from being able to access your data.
We observed PYSA exploiting exposed RDP services. This is not a tactic unique to this group and is used by many threat actors as a quick method to get an easy foothold into an environment. Securing RDP connections is important for all organizations, but it can be challenging for geographically dispersed and complex IT infrastructures.
- Understand Your Internet Footprint
External RDP services are often enabled to solve short term issues or for a development environment. These can fly under the radar of the usual security controls and may present an unexpected weak spot attractive to attackers. Conducting regular assessments of what services are exposed to the internet can be an effective method of identifying whether your exposure has changed. Ideally this should be conducted by an independent third party to ensure a thorough check. - Secure RDP Connections
RDP systems exposed to the internet will be vulnerable to brute force attacks, credential stuffing and potential vulnerabilities within the service. Best practice is to ensure all RDP services run within a virtual private network (VPN) solution to restrict external access. - Enable Network Level Authentication (NLA) for RDP
NLA requires authentication prior to a session being established. If NLA is not enabled, threat actors may be able to enumerate user accounts and fingerprint the Windows version. Vital intelligence for any motivated adversary.
PYSA is dependent on PowerShell scripts for reconnaissance, disruption and in some cases even encryption. Modern Windows operating systems include the Anti-Malware Scan Interface (AMSI) to enable anti-virus agents to detect and block malicious scripts. However, older operating systems, such as Windows 2012, do not include AMSI, so malicious scripts are unlikely to be detected and blocked. Therefore, it is important to assess the operating systems deployed within your environment and to make sure mitigation strategies are in place for any machines that do not conform to the hardening policy. Restricting the number of accounts that can run PowerShell may also reduce the ability of PYSA to operate as effectively within the network during their intrusion lifecycle.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.


