Through its cyber intake process, Kroll identified 23 ransomware incidents during the month of July 2019 that affected organizations across sectors, including service, retail and education.
Five of the incidents were attributed to Sodinokibi ransomware. Sodinokibi (also known as REvil or Sodin) is a newer ransomware strain that is packaged as ransomware-as-a-service (RaaS), much like its suspected predecessor GandCrab. (See GandCrab Connection discussion in this newsletter.)
Zero-Day Vulnerability Creates an Opportunity for Sodinokibi
According to the New Jersey Cybersecurity & Communications Integration Cell (NJCCIC), one foothold for Sodinokibi ransomware is a known zero-day vulnerability1 in the Oracle WebLogic Server component of Oracle Fusion Middleware (See CVE-2019-2725 Detail in the NIST National Vulnerability Database). The vulnerability allows malware to infect servers without relying on user interaction, as opposed to conventional methods of infection, such as malicious email attachments. Instead, the vulnerability allows attackers to gain access to a server using a web-based connection.
Managed Service Providers Targeted to More Efficiently Monetize Attacks
Another unique attribute of Sodinokibi is its effective use of managed service providers (MSPs) to spread the ransomware. Three of the five Sodinokibi cases Kroll identified in July involved the pushing of the ransomware from another vendor or IT provider into the clients’ networks. This is an efficient and effective way for ransomware to reach a large number of victims. In fact, the FBI released an alert in August 2019 noting “multiple U.S. companies suffering infection and encryption of file systems as the result of only one cyber intrusion.” MSPs that specialize in serving clients in specific industries, e.g., education or healthcare, can also unwittingly distribute the malware to a large swath of victims in a specific sector.
Associate Managing Director Thomas Brittain notes that many of the affected MSPs have been local or smaller vendors. “In the past, bad actors deploying ransomware were more opportunistic, conducting phishing campaigns hoping to encrypt the recipient. With Sodinokibi, however, cybercriminals are much more targeted, intentional and hands on. For example, in our casework we have seen two levels of reconnaissance in play. Once actors gain access to an MSP, they explore how many clients the MSP serves, the tools that the MSP uses for remote administration and patch management and the level of access in the client’s network. If the actors can gain access to the client’s network, they conduct a second phase of recon, enumerating the network to determine the total number of systems as well as any backups for deletion, and finally encrypt the available systems. The actors are then armed with knowledge on the number of clients and systems in each network served by the MSP, enabling them to assess the potential of the MSP or their clients to pay the ransom, usually driving a higher payout.
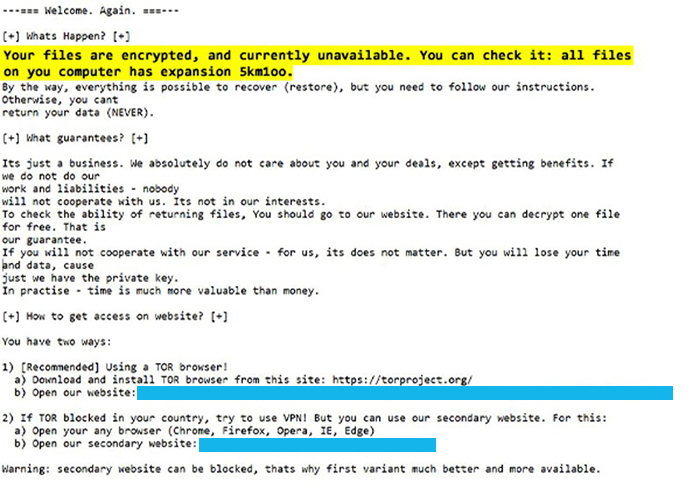
Figure 1 - Example of Sodinokibi Ransom Note
Technically Speaking
The GandCrab Connection
Since appearing on the scene in early 2018, GandCrab is estimated to have cornered a 50% share of the ransomware market at its height and likely affected more than 1.5 million victims globally, according to Europol. A June 2019 Europol press release described the GandCrab business model:
“Set as a ransomware-as-a-service licensing model, distributors could buy the ransomware on dark web markets and spread it among their victims. In exchange, they would pay 40% of their profit to the GandCrab developers and keep 60% for themselves.”
Sodinokibi ransomware made a splash at the end of May 2019 at the same time GandCrab ransomware brokers purportedly shut down their operations. On May 31, 2019, GandCrab actors announced their retirement in a dark web post, stating, “We have proved that by doing evil deeds, retribution does not come.”
The timing of these events led incident response teams to speculate that the GandCrab peddlers may have simply tinkered with their ransomware a bit and repackaged it into a new product. For example, according to the NJCCIC, “Some [Sodinokibi] attacks have followed up with an additional attack on the same target, distributing GandCrab v5.2.” The marketing of the variants is similar, and they are both used for RaaS and large-scale attacks.
Typical Observed Deployment Pattern
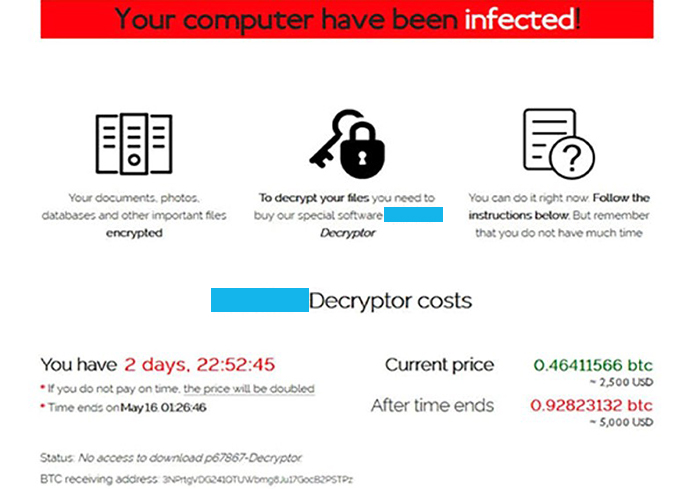
Figure 2 - Sodinokibi ransomware TOR site screenshot
Senior Director Scott Hanson provided the following attributes of Sodinokibi deployment that Kroll has observed in its cases. These techniques are also consistent with open-source reporting:
- Usage of PowerShell to execute the ransomware payload hosted on third-party sites, such as GitHub or Pastebin
- PowerShell is a native component of the Microsoft Windows operating system used by administrators. For this reason, a malicious PowerShell script is less likely to be blocked than other attacker methods.
- Deletion of volume shadow copies (typical of most ransomware)
- Volume shadow copies are the result of Windows technology that enable the system to create a snapshot of computer files or volumes while they are in use. Deleting volume shadow copies eliminates a source of backup data for restoring the system.
- Ransom notes have a naming convention of <random alphanumeric>-readme.txt (example in Figure 1)
- Desktop wallpaper image may be changed to a blue image with text including “All of your files are encrypted!” (example in Figure 3)
- Use of PsExec to push the ransomware from an initially compromised system to additional systems on the network
- PsExec is a command line tool that allows one to execute processes on other systems remotely.
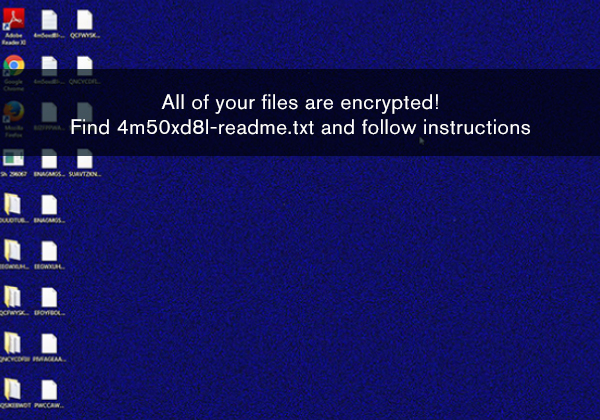
Figure 3 - Sodinokibi ransomware desktop wallpaper
Dark Web Sighting
A post on an open-source website noted the association of the RIG exploit kit with Sodinokibi. Palo Alto Networks defines exploit kit as “automated threats that utilize compromised websites to divert web traffic, scan for vulnerable browser-based applications, and run malware.”
Kroll searched the deep and dark web for references to the RIG exploit kit and discovered a post that advertises the sale of the RIG exploit kit for $60-$80 per day (Figure 4).
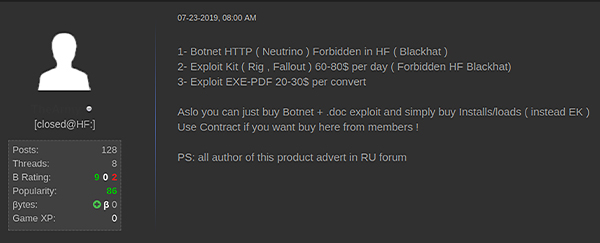
Figure 4 - RIG exploit kit for sale on dark web forum
Case Study
One incident that Kroll investigated demonstrates an insidious way that Sodinokibi can spread. Kroll’s client had remotely connected to one of their servers after realizing their digital surveillance system was not online. They immediately observed unusual text files residing on the desktop in addition to the background displaying a ransom note. A further inquiry revealed all seven of their servers had been encrypted with Sodinokibi ransomware. The affected servers were remotely administered by a third-party digital surveillance company, who alerted the client they had also been infected with the ransomware.
Kroll Experts Corner: Best Practices for Mitigating Sodinokibi
Following are insights from Kroll experts Thomas Brittain, Scott Hanson, Michael Hill and Cole Manaster on how to better defend against Sodinokibi.
- Patch Systems
Confirm that systems have been patched for the Oracle WebLogic Server vulnerability that is targeted by Sodinokibi ransomware. - Move Backups Offline
Offline backups are hard for adversaries to touch. But remember, if your online systems sync to your backups, this provides an avenue for the malware or actor(s) to delete your backups. - Monitor Remote Connections
Deploy a monitoring solution that can provide visibility on the activity of remote connections and software, such as Remote Desktop Protocol (RDP). - Employ 2FA
Apply two-factor authentication (2FA) to user login credentials and implement least privilege for file, directory and network share permissions.
Key Considerations When Engaging an MSP
- How is the MSP securing connections to your system?
- Are they leveraging 2FA/MFA for remote connections into your environment?
- What patch management schedule does the MSP follow?
- Will the MSP handle backups and recovery in the event of a ransomware attack?
It’s important to have a sound understanding of how an MSP is protecting access to your environment and the full scope of their service offering. This knowledge will enable your team to plan a comprehensive security, crisis communications and disaster recovery strategy that includes securing external network access, patch management, online/offline backups and an incident response plan.
Source:
1 Oracle has since released a patch available here.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.