In May 2020, Kroll began observing an increase in compromises related to vulnerabilities in Telerik user interface (UI) software, a spinoff of Telerik’s web software tools which provides navigation controls. The vulnerability, which is outlined in CVE-2019-18935, involves a .NET deserialization vulnerability in the software that allows for remote code execution. Kroll observed more than a dozen cases in a short span of time in which attackers targeted the Telerik vulnerability to deploy remote access tools or credential harvesting software and then gain remote access to the client’s network. The most often targeted clients observed by Kroll within the sample timeframe were in the healthcare and government sectors (Figure 1).
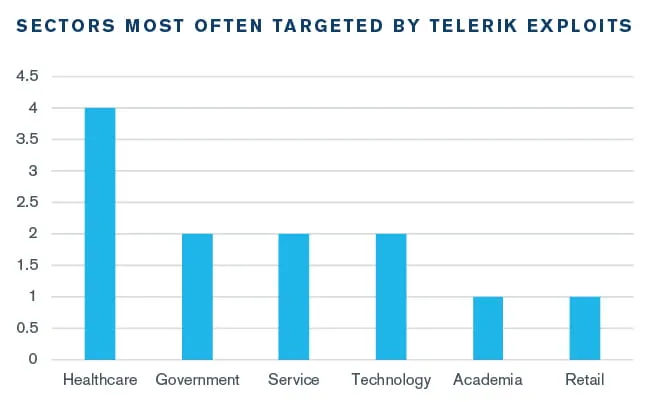
Figure 1 - Sectors Most Often Impacted by Telerik Exploits
How Do Threat Actors Exploit the Telerik Vulnerability?
The deserialization attack enabled by CVE-2019-18935 is different from the previously exposed encryption flaw in CVE-2017-11317, which allowed unrestricted file uploads. In the deserialization attack, rather than submitting the expected Telerik.Web.UI.AsyncUploadConfiguration type with rauPostData, an attacker can submit a file upload POST request specifying the type as a remote code execution gadget instead. This gives attackers the ability to execute software, code or webshells indiscriminately within the webservice.
Kroll was able to pinpoint attacks by examining available forensic evidence and most critically, web server access logs, looking specifically for unique user-agent strings and IP addresses previously flagged by our threat intelligence team. Investigating those strings and activity tied to their interactions with internet facing servers revealed suspiciously uploaded files, ranging from .aspx, .js, to .zip content. Kroll’s analysis of identified files revealed a range of capabilities across different impacted systems from code injection and remote access to credential harvesting.
Anthony Knutson, Senior Vice President in Kroll’s Cyber Risk practice, provided more details: “Specifically in the webshells, our engineers were able to recreate what the threat actor would see when traversing specific pages and demonstrate how these webshell files could go undetected by requiring the specific user-agent string we mentioned. Without that user-agent string, the page would load as an HTTP 404 error, and the webshell would not activate.”
Devon Ackerman, Managing Director and Head of North America Incident Response, added: “Like most webshells leveraged by attackers, these shells provided the unauthorized actors with abilities ranging from direct SQL database access, to file read/write capabilities, to operating system-level remote command prompt and PowerShell access.”
Reported Large-Scale Telerik Vulnerability Exploitation
In early June, Australia suffered a large volume of state-sponsored attacks related to the Telerik UI vulnerability. The government observed advanced persistent threat (APT) scanning for unpatched versions of the Telerik vulnerability and leveraging publicly available exploits to attempt to exploit these systems. “The actor has been identified leveraging a number of initial access vectors, with the most prevalent being the exploitation of public-facing infrastructure — primarily through the use of remote code execution vulnerabilities in unpatched versions of Telerik UI,” the report stated.
According to recent reporting by the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC), a group dubbed Blue Mockingbird recently infected thousands of computer systems via the Telerik vulnerability. “The group conducted a cryptocurrency mining campaign by targeting public-facing servers running ASP.NET apps using the Telerik framework. By exploiting CVE-2019-18935, the group was able to install a web shell in the compromised server and then used a privilege escalation tool to gain accesses needed to modify server settings and maintain persistence,” the report stated. Devon Ackerman, Managing Director in Kroll’s Cyber Risk practice, added, “In Kroll’s estimation, for the investigations where actor groups have leveraged the Telerik vulnerability to push in cryptocurrency mining operations, the activity was noisy and burdensome to the impacted systems. In every case that Kroll investigated involving this methodology, the client’s IT and security team had already noted the system resource impact tied to the miners—it wasn’t stealthy, it wasn’t a structured attack, but it was noisy, like a thief stumbling through a victim’s home knocking over lamps and cabinets alerting everyone within ear shot of their presence.”
Examples of Telerik Exploits in Recent Cases
- Kroll responded to one example incident in which an e-commerce client had a downstream customer report instances of fraud after using a credit card on their website. In early May, after several days of review, the client found a malicious script that captured cardholder data (more specifically it captured content of the visitor’s typed in or auto-filled check out form input) upon checkout. The client assessed that the Telerik vulnerability had been exploited to introduce the malicious script. They removed it, but by that point, the script had impacted a significant number of cards due to the client’s daily e-commerce site traffic. The Kroll team proposed validating the scope of the client's exposure, conducting a root cause analysis and reviewing logs to determine whether any additional scripts or web shells were introduced.
- In another investigation, a Kroll client started receiving complaints from customers whose banks informed them that fraudulent charges were originating from the client organization. A couple weeks before the attack, one of the client’s IT vendors advised that they had identified the Telerik vulnerability within their vendor-managed database, which allowed code to be remotely executed in an unauthorized manner. The Kroll team proposed conducting an investigation into unauthorized access of data contained in or entered into the client's website and to review systems for possible acquisition of same.
- Another client had cryptomining software deployed in their environment. The Telerik vulnerability was used to upload malicious files and run malicious binaries allowing the escalation of privileges in an Internet Information Services account from an internet accessible server. With elevated privileges, the actor(s) retrieved cached credentials from system memory using tools such as Mimikatz which allowed further access the network, lateral movement between servers and eventual staging and deployment of the XMRig cryptocurrency mining software.
Kroll Experts Corner: Best Practices for Preventing Telerik Exploits
The following recommendations, provided by Kroll experts Michael Quinn and Devon Ackerman, should be taken into consideration to prevent exploits directed at the Telerik vulnerability:
- Enforce a consistent vulnerability and patch management program focusing on internet-facing infrastructure
- Conduct periodic penetration testing or red team exercises
- As mentioned in several of our previous articles, deploy multi-factor authentication for all internet-accessible remote access services
- Ensure adequate Windows event logging and forwarding and system monitoring is in place
- Update Telerik UI to the latest version available. Telerik is also included with third-party software, such as the last case Kroll worked on. In this instance, third-party vendor software should be updated and remain in contact to ensure the vendor is aware.
- Search for the version of Telerik if unknown. This can be accomplished using tools such as grep, PowerGrep or the “strings” binary. If Telerik can be updated, isolate the host, bring offline or monitor the system more thoroughly.
- Look for connections to the following URL within the web server logs: /Telerik.Web.UI.WebResource.axd?type=rau
Leave Nothing to Chance
Managing an ever-expanding list of vulnerabilities takes considerable resources and it’s especially hard to determine which vulnerability deserves priority attention. For internal teams burdened with a host of other priorities and a remote workforce, support from dedicated experts who have the frontline expertise, resources and technical skills to assess your exposure can greatly reduce your risk profile. Talk to a Kroll expert today via our 24x7 hotlines or contact form.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.


