Malware Trends In Intelligence Collection

Malware Trends Analysis
In December 2024, Cyberhaven reported that their Chrome extension had been compromised, with malicious code inserted into the extension that sought to exfiltrate cookies, sessions and other browser credentials. The company noted that a phishing attack on an employee enabled the incident. This gave the threat actor credentials to their Google Chrome Web Store and the ability to upload the malicious code.
It became clear that the malicious code was information-stealing malware designed to harvest credentials, including passwords, cookies, tokens and other sensitive information entered into websites that the user browsed.
On the same day, the Kroll Security Operations Center also observed similar behavior, but from an end user perspective, in which the legitimate extension Bookmark Favicon Changer (FC) that was previously installed was updated to include the malicious code seen in the Cyberhaven reporting. The extension was observed attempting to connect to the IP address 149[.]28.124.84, which hosted the malicious domain bookmarkfc[.]info. This IP address was also used during the Cyberhaven extension compromise. Both extensions were updated on December 25, 2024, with a more recent update appearing for BookmarkFC on December 30, 2024, likely to remove the malicious code.
Kroll Threat Intelligence conducted further investigation into the IP address and identified an additional list of domains hosted on that IP address that are likely mimicking other compromised browser extensions.
One particularly interesting domain in this list appears to mimic Censor Tracker, which has a significant user base. This extension was last updated on December 25, aligning with the other observed malicious code updates. The range of extensions displays the potential widespread impact to users, particularly with the large user bases of some of the extensions.
It is worth noting that one of the mimicked extensions, Moonsift, had not been updated on the Chrome store since October 3, 2024, which was before this campaign. This suggests that either the domain registration is preemptive for future compromise or the threat actor was unsuccessful in phishing for credentials against the developer.
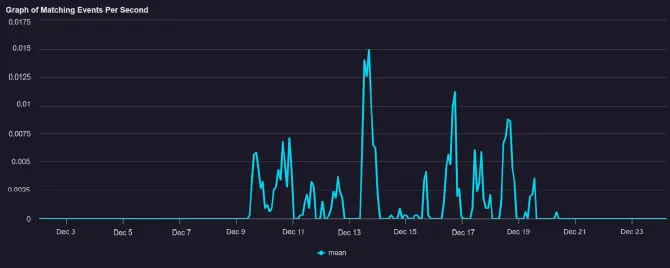
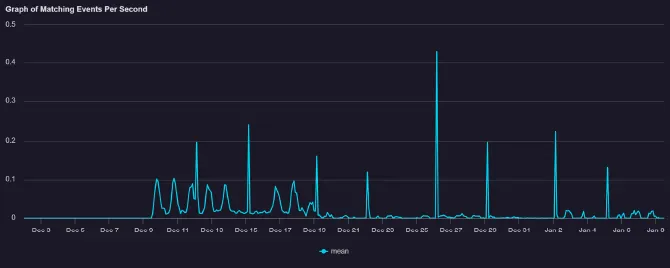
Based on initial findings from Kroll’s investigation, it appears that this campaign started around December 25, 2024. However, after conducting threat hunting across managed services customers, Kroll identified malicious activity beginning on December 9, 2024, in both EMEA and the U.S.
The information displayed in the graphs below shows logged events that contained either a Domain Name System (DNS) request or connection to a malicious domain or IP address that Kroll collated from firsthand observations or open-source reporting.