January Threat Intelligence Spotlight Report
by George Glass, Keith Wojcieszek


When mobile phone data is required to serve as evidence, Kroll ensures that no relevant information is overlooked. Our mobile phone forensics specialists can assist at any stage of an investigation or litigation to analyze key digital clues and quickly and defensibly uncover critical information.
With a global network of over 650 forensic examiners and laboratories across 19 countries, we respond to more than 3,000 incidents a year and work with over 100 law firms across the globe. Our highly experienced mobile forensics practitioners maintain SANS and other industry certifications associated with a range of mobile device forensics software. The Kroll team includes certified Cellebrite instructors, thought leaders and lecturers on digital forensics courses. We deploy forensically sound, best-practice methodologies to gather data for electronic investigation and forensic analysis, or forensic discovery.
With a reputation founded on extensive experience in forensically sound investigations and electronic data discovery, our mobile phone forensics services deliver high-caliber insight when it matters most.
To you, your network of mobile devices is a critical business asset. To a cybercriminal, it’s a source of valuable data and a potential point of access to your financial, cloud, and business assets and intellectual property. From smishing to malware to malicious apps, the security risks associated with smartphones and other mobile devices are significant. The rise in recent years of remote and hybrid working has further increased this challenge for organizations, combined with bring your own device (BYOD) and security corporate mobile inventories.
Retrieving potentially incriminating information at quickly and safely from a seized mobile phone is a complex process that presents many risks. Kroll’s approach draws on extensive experience, ensuring that critical evidence is accessed securely and within your required time frame. As experts in forensic mobile phone analysis and mobile phone data recovery, our team follows a proven process, based on industry standard chain of custody (CoC) guidelines. Our collection methodologies and CoC documentation meet the stringent standards required for acceptance in court.
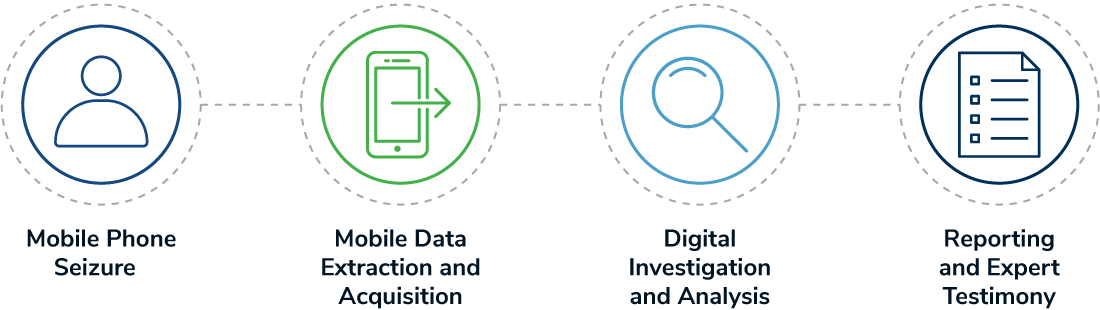
With potential evidence at stake, this stage is critical to the success of the mobile phone forensics process. Each device should be handled and stored carefully to ensure that as much data as possible is preserved. During this phase, the data held on the device is vulnerable to two key risks: lock activation and network connection. Investigators protect against this by isolating the network and the device using the following methods:

Device shutdown can alter files and lead to the loss of valuable evidence. Investigators must mitigate this risk by keeping the phone on and putting it in airplane mode while it is transported.

The use of a Faraday Enclosure, a container designed to isolate mobile devices from any networks, accompanied by an external power supply, enables investigators to securely move mobile devices to the laboratory without risking the loss of any data.

A Faraday Bag works in the same way as a Faraday Enclosure to prevent signals from being sent and received by the device, ensuring that the data it contains is not tampered with.
Once the mobile device has been seized and secured, investigators then extract the evidence by duplicating the files on it, using a software imaging tool, a process referred to as acquisition. Creating a duplicate in this way maintains the integrity of the original files so that it is suitable for use as evidence. After the media file with the duplicate has been carefully stored, it is verified in a process called “hashing” to ensure that all the data in the file is in its original state.
Regardless of the operating system your organization relies on, Kroll’s seasoned experts can provide in-depth mobile phone data forensics and analysis. Our team understands the data extraction challenges, risks and opportunities presented by the two main types of operating system.
As the first step of every digital investigation involving a mobile device(s), the forensic expert needs to identify:
At this stage, the evidence collected is presented to other forensic examiners, if appropriate, or to a court that will determine its relevance to the case. Depending on an organization’s specific requirements, Kroll’s experts can author declarations, affidavits and any expert reporting necessary. We can also serve as expert witnesses, providing expert testimony in presenting findings to judges, juries and arbitrators, with many of our team having served as special masters at the court’s appointment.
Our experts are recognized for the quality and independence of their insight and have been appointed as expert witnesses on the world’s largest and most complex disputes. We have extensive testifying experience in business and commercial disputes that are resolved through litigation, including in federal courts in the U.S. and Canada, the U.S. state courts, the U.S. Tax Court, the Tax Court of Canada, bankruptcy courts, the International Trade Commission and the UK High Court.
Kroll’s cyber risk retainer enables organizations to manage and minimize the potential impact of mobile device fraud. Delivering more than a typical incident response retainer, our cyber risk retainer includes elite digital forensics and incident response capabilities, with maximum flexibility for proactive and notification services.. The Kroll cyber risk retainer guarantees expedited response as well as notification and proactive services to minimize the impact of an incident. Learn more.
Incident response, digital forensics, breach notification, security strategy, managed security services, discovery solutions, security transformation.
Kroll's computer forensics experts ensure that no digital evidence is overlooked and assist at any stage of an investigation or litigation, regardless of the number or location of data sources.
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Whether responding to an investigatory matter, forensic discovery demand, or information security incident, Kroll’s forensic engineers have extensive experience providing litigation support and global eDiscovery services to help clients win cases and mitigate losses.
Kroll's expertise establishes whether data was compromised and to what extent. We uncover actionable information, leaving you better prepared to manage a future incident.
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
Visit Booth 523 for one-on-one insights on advancing your legal operations through industry-leading transformational programs.


Join Kroll experts at RSAC 2025 in San Francisco. Stop by booth 842 in the South Expo Hall to meet our team.

Join our Cyber and Data Resilience experts at Infosecurity Europe in London, June 3–5. Stop by stand D45 to meet our team.
