A strong cyber security strategy is built on a foundation of knowing the specific threats your industry faces and what critical business data is being maintained on your network. A risk assessment conducted by independent cyber security experts can identify
- the various measures that need to be in place to satisfy the three pillars of cyber security discussed below and
- the pragmatic steps that can mitigate any identified vulnerabilities.
Penetration tests and vulnerability scans can also provide valuable insight into network weaknesses just waiting to be exploited by cybercriminals.
Creating a Strong Cyber Security Strategy
What steps should a retailer in the cannabis industry take to build a strong cyber security strategy that gives customers peace of mind that their sensitive and personal data is being protected? By developing a strategy based on the three pillars of cyber security — People, Policies and Technology — cannabis businesses will be in a much better position to reduce their vulnerabilities and mitigate the various threats targeting their networks.
First Pillar – People
As previously stated, end-users are the primary vector for cyberattacks. However, employees can also be your first line of defense if properly trained. Marijuana retailers must educate their employees on current trends of attacks that cybercriminals use to compromise accounts, leading to exposure of sensitive data. Some best practices include the following:
Implement a security awareness training program and deliver training to all employees, especially senior management, as many of today’s cyber scams target executive-level employees.
Build training programs that include phishing and social engineering tests that expose employees to the types of scams favored by cybercriminals; highlight the damage that could result to a business if these types of attacks go unrecognized as attempts to compromise the network.
Second Pillar – Policies/Processes
Many of today’s cybercrimes are successful not because malware or code injection attacks are so sophisticated, but rather because mature cyber security policies are absent or security processes are not being followed. Cybercriminals target companies every day, and marijuana retailers possess valuable information that criminals would love to access. To build a mature cyber security strategy, one needs to develop or revise security policies to mitigate prevailing cyber threats. Here are some policy/process suggestions:
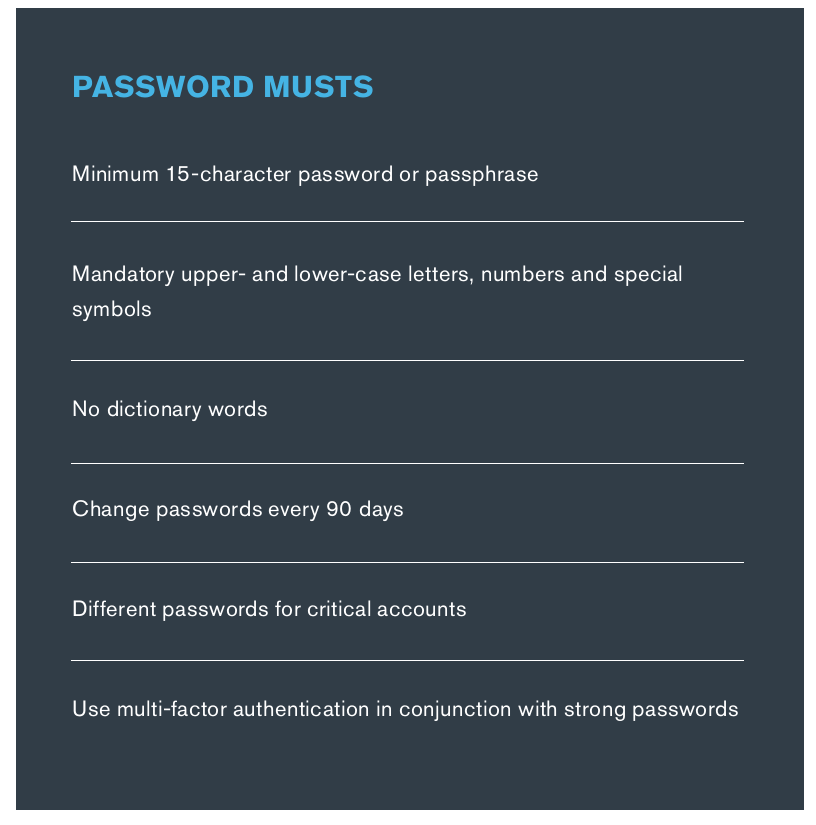
- Password Policy
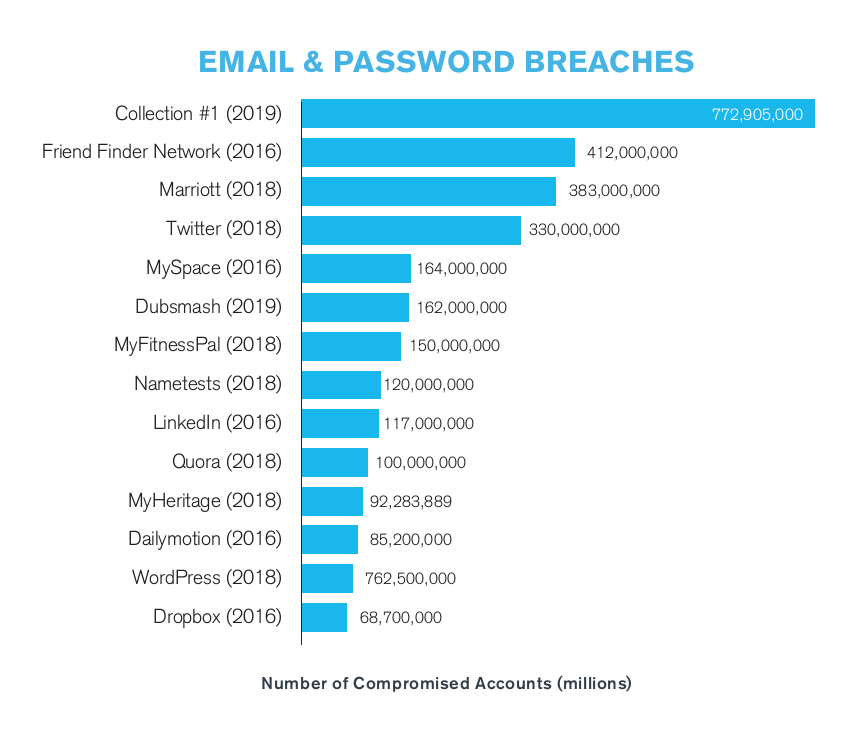
Credential theft and password reuse are some of the most common avenues that cybercriminals leverage to get access to a victim’s network. Due to the sheer volume of data breaches over the years, there are now literally billions of stolen emails and passwords being traded on dark web forums.
- Multi-Factor Authentication (MFA):
Access requests should be authenticated through methods such as SMS, push-notification or hard token. MFA is especially critical when accessing VPN, email and any database containing sensitive data. - Acceptable Use Policy
Restrict employees’ access to freely surf the internet and visit suspicious websites, which can pose a risk for infecting your network from a “drive-by” malware attack (i.e., downloading a website that has been compromised with embedded malware). - Least Privilege Policy
Only provide your employees with access to the platforms and databases on your network that they need to perform their responsibilities. Restrict administrative rights to only those who absolutely need it and require privileged users to utilize a separate ‘admin’ account when they need to perform administrative functions. This type of role-based authorization may reduce the level of exposure to sensitive data if an account with limited access is compromised. - Encryption Policy
Encryption is a great means to protect confidential or sensitive information from being accessed by cybercriminals. States that have legalized cannabis for medicinal purposes require the use of encryption when dispensaries report transactions from patients to appropriate state health or cannabis commissions (similar to HIPAA and PIPEDA requirements). Individuals who are authorized to receive medicinal marijuana are issued state medical cards that are entered into a database shared by dispensaries. The database provides the authorized quantity of medicinal marijuana that can be sold to a patient, similar to other prescription medications.
Although there is no regulation regarding the tracking of individuals purchasing marijuana for recreational purposes, dispensaries are required to send electronic notification of the RFID codes of the marijuana product sold to comply with “Seed to Sale” regulations. Most states limit the quantity of recreational marijuana that can be purchased/possessed by an individual at one time. However, there are no central databases to document this information that would alert a dispensary that a customer had already exceeded his/her daily purchase limit. This type of tracking/enforcement concept is being discussed in various state legislatures where cannabis has been legalized.
Marijuana retailers should establish a policy that requires the encryption of any sensitive data maintained on their network or data stored in temporary memory files (susceptible to memory scraper malware). An encryption policy would facilitate future compliance with any tracking/enforcement legislation, as well as provide a layer of security to protect sensitive customer data from cybercriminals. - Bring Your Own Device (BYOD) Policy
With so many employees now working remotely, whether on a full- or part-time basis, employees often use their own devices to log into the corporate network to conduct their work. A lack of a restricted BYOD policy can result in employees infecting the corporate network with malware contained on their personal devices. A solution to this added risk would be to enforce the use of a VPN when connecting to a corporate network. - Incident Response Plan (IRP)
Because we exist in a world of “assumed breach”, it is important that every cannabis dispensary have an Incident Response Plan (IRP). At a minimum, the IRP should define what constitutes a cyber “incident” and identifies the members of the Incident Response Team as well as their assigned roles and responsibilities when dealing with an incident. Once a comprehensive IRP is established, an annual table-top exercise, facilitated by independent cyber experts, should be conducted to enable the Incident Response Team to practice how they would respond to a cyber incident in accordance with the plan.
Third Pillar – Technology
Many effective technical solutions exist that can help organizations, including cannabis retailers, protect their networks and alert responders to suspicious activity that is either attempting to take hold or already executing on their network. Some of these essential tools and best practices include, but are not limited to, the following:
- System Hardening
- Implementation of configuration changes to enhance security by eliminating potential attack vectors.
- Patch Management
- Ongoing installation of security updates for hardware and software assets.
- Firewall
- Device to manage access to an organization’s network.
- Intrusion Detection System (IDS)
- Device to monitor a network for malicious activity or policy violations.
- Endpoint Detection and Response (EDR)
- Solution to monitor processes on network computer endpoints for suspicious or malicious activity.
- Data Loss Prevention (DLP)
- Solution to monitor, detect and block sensitive data in use, in transit or at rest in order to prevent data leakage.
- Mobile Device Management (MDM)
- Solution to monitor, manage and secure employee mobile devices.
- Dark Web Monitoring
- Solution to search the dark web for personal information, stolen credentials, intellectual property, etc.
- Third Party Risk Assessment
- Solution to assess the security program maturity for third party organizations that access or store data on an organization’s behalf.
Light Your Path
The cannabis industry has reached a tipping point and exponential growth is ahead. Protect your business, safeguard your investment and anticipate regulatory requirements with the help of Kroll. Our experts can help enhance your cyber and physical security, conduct due diligence, and assess the value of dispensaries, grow facilities, and more. Get in touch with a Kroll expert today.
