While millions in the U.S. are planning on a refund this tax season, cybercriminals globally are working to line their own pockets with those refunds. Based on Kroll’s investigative experience, we expect cybercriminals to rely on many of the same tactics that have proved successful earlier, such as phishing campaigns, stolen data and account takeovers.
Still, due to the constant evolution of the cybercriminal landscape, each tax season in the U.S. and other countries tends to have its unique twists. Here are a few new developments that organizations and individuals may encounter this year.
What’s New This Tax Phishing Season?
Phishing campaigns that manipulate unsuspecting victims to share their personal or corporate Form W 2s with a fraudster are not new. However, according to open-source reporting, a worrisome take this tax season is the banking Trojan Emotet, which has the potential to compromise an organization’s entire network.
In this campaign, a user is lured into clicking on an attachment or link that purports to contain a Form W-9. Once the victim clicks the link or attachment, his/her system becomes infected with the Emotet malware. In addition to harvesting user credentials, Emotet malware is often used as a first-line dropper in a phased Ryuk ransomware attack as Kroll, a division of Duff & Phelps, has previously reported. Ryuk ransomware was the most frequently reported ransomware variant in Kroll incident response cases in 2019, accounting for approximately 64% of all ransomware cases.
Another ransomware variant, Maze, is associated with a tax-centric malspam campaign that hit German and Italian users in late 2019. Victims received a phishing email message supposedly from the German Ministry of Finance or Italian Revenue Agency, which directed them to click on an attached Word document for instructions on how to request a refund. When users clicked on or opened the document, malicious code installed Maze ransomware on their computer.
Maze has gained significant notoriety within the past three months, for becoming the first ransomware variant whose creators have publicly posted exfiltrated data of victim companies, who do not pay the ransom.
Get Your W-2s (On the Dark Web)
A classic tax season phish lures unsuspecting victims to forward an organization’s entire set of W-2 forms to cybercriminals in bulk. Actors will then act quickly to monetize the W-2 forms on various underground forums.
Kroll identified one such posting on carding site Crd2Club (Figure 1). The actor claims to have access to over 350 full profiles for 2019 U.S. tax return filings, including Form W-2s; a December 2019 paystub to help calculate annual wage; and a Form 1040. Numerous data points are also included in a profile, such as employer identification number (EIN), state ID number and Internal Revenue Service (IRS) Identity Protection PIN.
The actor alleges that data is “fresh and valid” and promises would-be buyers the “opportunity to make between USD 7,000 to USD 14,000 per filing.”
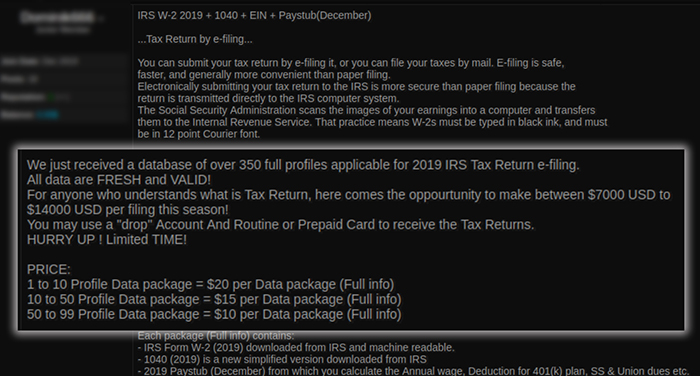
Figure 1: Crd2Club IRS W-2 Filing Advertisement
Account Takeover, Tax Season Style
With 90% of U.S. taxpayers filing their taxes online, cybercriminals have another lucrative avenue to exploit. For example, Kroll has observed many cases where cybercriminals leverage weak or stolen credentials to take over online tax preparation software.
These account takeovers primarily occur via two different approaches: by targeting an individual taxpayer or by targeting professional services companies, such as accounting firms who have bulk access to client tax information. In 2019, the professional services category, which includes accounting firms, accounted for nearly 15% of reported Kroll incident response cases, which reflects that these firms are increasingly vulnerable to such attacks.
During the 2019 tax season, Kroll responded to multiple cases involving accounting firms in which tax information was specifically targeted. In one instance, an attacker compromised an employee’s email account and leveraged that to access Smart Vault, an online document sharing system, where the company was storing its client’s electronic tax documents. The attacker attempted to file fraudulent tax forms using information from these documents.
In another instance, a threat actor exploited vulnerabilities within the accounting firm’s remote desktop protocol application, to gain access to sensitive information, and file 53 fraudulent state tax returns.
The online proliferation of hacked account credentials was redefined in early 2019, when the Collection 1-5 data dumps became the largest breached data dump to be made publicly available. Experts estimate that the dataset contains username and password data for around 2.2 billion accounts.
Individuals who reuse passwords across platforms, including those used to prepare taxes, are vulnerable after such large exposures. Hackers will often systematically check credentials across multiple sites until they get a hit, then sell those valid credentials on an underground marketplace.
One such market, previously reported on by Kroll, has recently been selling access to compromised personal computers (Figure 2). These computers have been targeted, compromised and listed for illegal use for a small fee. Once a user purchases access to that compromised computer, they also have access to every resource contained on that device, such as any website with a saved login credential(s) and password(s).
Kroll’s review of the market’s offerings revealed hundreds of listings that included tax filing platforms as an available resource. Cybercriminals with access to such a resource may be able to access the account and populate the software with information from last year’s filing without needing access to a W2.

Figure 2: Sample Saved Password List that a Cybercriminal May Access from Underground Markets
What Can You Do?
The IRS recently launched its Identify Theft Central platform as a resource for taxpayers, tax professionals and businesses, during the 2020 tax season. This streamlined platform was created to combat identity-theft-related tax fraud; to educate consumers and businesses on identifying identity theft; and what to do if you or your organization becomes a victim.
Keith Wojcieszek, Managing Director at Kroll, recommends organizations be particularly alert during the tax season and follow best practices for cyber hygiene, such as the following:
- Educate personnel, especially finance and human resources staff, on the increasing risk of tax-related phishing campaigns during this time frame, which can also lead to other crippling cyberattacks such as ransomware
- Leverage resources like the IRS Identity Theft Central platform, to stay abreast of current trends and steps to be taken if you become a victim of tax fraud or identity theft
- Enforce responsible password management:
- Do not allow passwords to be reused across multiple platforms/applications, and remind staff to follow the same practices with their personal online accounts
- Set complex passwords with at least eight characters and a mix of special and alphanumeric characters
- Consider implementing next-generation antivirus solutions and endpoint threat monitoring and response capabilities
- Ensure your incident response plan is up-to-date, particularly regarding potential breach notification responsibilities
Stay Vigilant for Schemes and Compromised Data
Individuals and organizations must be on their guard for common schemes that lead to tax fraud, such as phishing email messages and smishing (i.e., phishing via a mobile SMS text message). In addition to exercising a healthy dose of skepticism and caution, when receiving tax-related messages, individuals should ensure antivirus solutions and software patches are up to date on all their devices.
Deep and dark web monitoring can also provide a critical alert to organizations that employees’ tax-related data has been compromised. This knowledge may help an organization address other potential intrusions in their networks before they can escalate. Organizations may also want to consider providing employees with identity theft monitoring and remediation solutions, in the event their sensitive data has been breached.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
