The number of ransomware cases investigated by Kroll, a division of Duff & Phelps, quadrupled over the last seven months of 2019. In fact, ransomware surpassed business email compromises as the threat type most commonly reported to Kroll during the month of September, and maintained this dubious monthly distinction throughout the end of the year.
While Ryuk was the most frequently reported ransomware, 13 new variants appeared in Kroll cases following the summertime ransomware spike. But apparently, threat actors are no longer content with simply creating new ways to lock up data; recently, they have raised the stakes by adding data collection and exfiltration to their arsenal of tactics, techniques and procedures (TTPs).
Ransomware Variants
Dharma/CrySIS | Actin |
Phobos | Locky |
RobbinHood | MedusaLocker |
Ryuk | Megacortex |
SamSam | Rapid |
Snatch | |
Sodinokibi | |
Tflower | |
WannaCry | |
DoppelPaymer | Adage |
Evil Locker | Bad Day |
GandCrab | Buran |
GlobeImposter 2.0 | Defray777 |
Hermes | FabSysCrypto |
Matrix | FileCoder |
Mr.Dec | Horrible Morning |
Nozelesn | I-encrypt |
“In Kroll’s investigative experience, and according to open- and closed-source intelligence, ransomware actors were traditionally more interested in collecting ransoms than in collecting sensitive data. That all changed in November 2019,” said Ben Demonte, North America Leader of Kroll’s Cyber Risk practice, who has spoken on the issue at recent industry events.
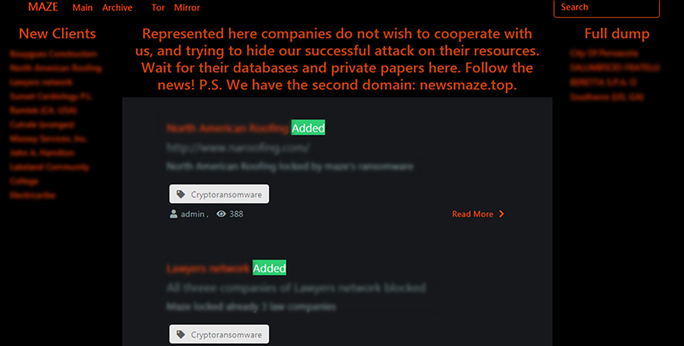
The group behind Maze ransomware publicly exposed a victim company’s data in November 2019 after the company failed to pay the ransom. In mid-December, the same group created a public website naming what it claims to be additional victim companies and threatening to expose their data if ransom demands were not met (Figure 1). As of early 2020, the group has made multiple updates to this “shaming site”, both removing companies and adding new ones. Since its inception, the site has publicly outed approximately 29 companies.
Figure 1 – Maze Ransomware Shaming Site Screen Capture
Threat actors behind other common ransomware variants may be following the same path. In mid-December, an actor known as the operator of REvil (aka Sodinokibi) ransomware claimed that each of their attacks will be “accompanied by a copy of commercial information.” According to the post, if payment demands are not met, the data will be exposed. At this point in their post, they added the phrase “GDPR,” possibly playing on organizations’ fears that such exposure could incur GDPR fines.
Prepare for a Bumpier Ride Ahead
Do these recent events constitute a long-term change in TTPs of ransomware gangs? Or are these particular threat actors making a quick bid for significant cash that will precede a retirement announcement? So far, the answer remains to be seen, but clues have emerged.
Earlier this year, the GandCrab operators announced their retirement with a proclamation that they had earned more than USD 150 million per year, stating “we proved that in a year you can earn money for a lifetime.”
Kroll experts have previously offered best practices for ransomware mitigation and recovery. “Multifactor authentication, least privilege policies, vetting and securing all remote access applications (including connections with managed service providers and other third parties), creating and protecting backups, and reinforcing a cyber security culture throughout the enterprise should be at the top of every organization’s security list,” added Ben.
But in this uncharted landscape, organizations must be able to simultaneously grapple with regulatory requirements related to data breach notifications. According to Ben, “I don’t think there’s a worse time than in the midst of a ransomware attack to have to assess whether – or how many – aspects of the organization’s network have been compromised. Aside from simply not having access to systems, recovery efforts can often obscure or obliterate vital forensic evidence. In either case, it takes careful investigation to determine the extent of potential data exposure. This includes identifying attack vectors, other malware introduced into the environment, where actors may have moved (e.g., email accounts; collaborative platforms (e.g., SharePoint); finance, human resources or ERP systems; on-premises or cloud databases; to name a few) and the types of data viewed and/or exfiltrated (PII, PHI, PCI-regulated, etc. So, one ransomware event can ultimately lead to myriad, time-sensitive, individual and regulatory notifications.” These problems require different skill sets and mitigation techniques in order to meet critical deadlines.
Kroll Experts Corner – Best Practices for Data Exposure
Following are some insights from Kroll experts on mitigating data breach exposure from ransomware attacks.
Now that ransomware attacks bring the simultaneous prospect of a data breach, organizations must understand that today’s stricter, and often, multijurisdictional data privacy laws will also start the clock ticking for potential notification. In addition to recovery activities, initial response efforts will likely need to include forensics and eDiscovery to ascertain the type and scope of data affected.
Managing Director Michael Quinn commented that the value of incident response planning cannot be overemphasized in these situations. “Once you realize your data or network has been compromised, there is no time to spare. If you have taken time to create, and regularly test, an incident response plan, your team will be better able to react quickly and confidently. Staff will know the experts and other resources to call in, as well as when and how to escalate response to the next level if needed,” explained Michael.
“Leaders may also want to consider incident response retainers, which can accelerate recovery while taking even more uncertainty out of the equation. All this advance work and incident response planning may pay additional dividends as part of a defensible cyber security strategy when communicating with regulators and other stakeholders if notification becomes necessary,” he added.
According to Brian Lapidus, global leader of Kroll’s Identity Theft and Breach Notification practice, most inhouse teams will need the help of experts in diverse disciplines for their notification efforts to be effective and compliant. “First, it’s imperative to determine the exact scope of a breach incident,” said Brian. “We have seen where original estimates of affected individuals have been substantially higher, and in some cases lower, after the forensics reports come in. Experts in data scrubbing and deduplicating can further refine the scope of notification.”
Brian continued, “The characteristics of the data – is the data generally identifying, protected health information or credit-related? – will also affect notification, as will the jurisdictions where affected individuals reside. With many data privacy laws compressing the timeframe for notification, being able to rely on experts who can expedite overall decision-making and the operational essentials of notification can bring enormous peace of mind.”
Breach counsel, crisis communications professionals and a breach recovery team who can manage the entire cycle of notification – from letters, FAQs and websites to local and international call centers to identity theft monitoring and restoration services to auditable reports for regulators – can better protect your organization’s reputation, brand and bottom line.
Validate Your Readiness
A ransomware attack can make response and recovery exponentially more complex and costly when compounded by a data breach. Speak with a Kroll expert today to learn how we can help you strengthen your overall cyber security and mitigate potential data breach exposure.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.